Any embedded system requires some degree of security. It may be something basic as locking down a programming port or something advanced to safeguard the system from a hacker. An efficient security solution is integral to embedded software development, no matter the scale. There are 5 elements to secure embedded systems. This blog will explore each element in detail and explain how they protect the system from security threats.
Establishing a secured system relies on the following:
- Hardware-based isolation
- A Root-of-trust
- A secure boot solution
- A bootloader
- Reliable storage
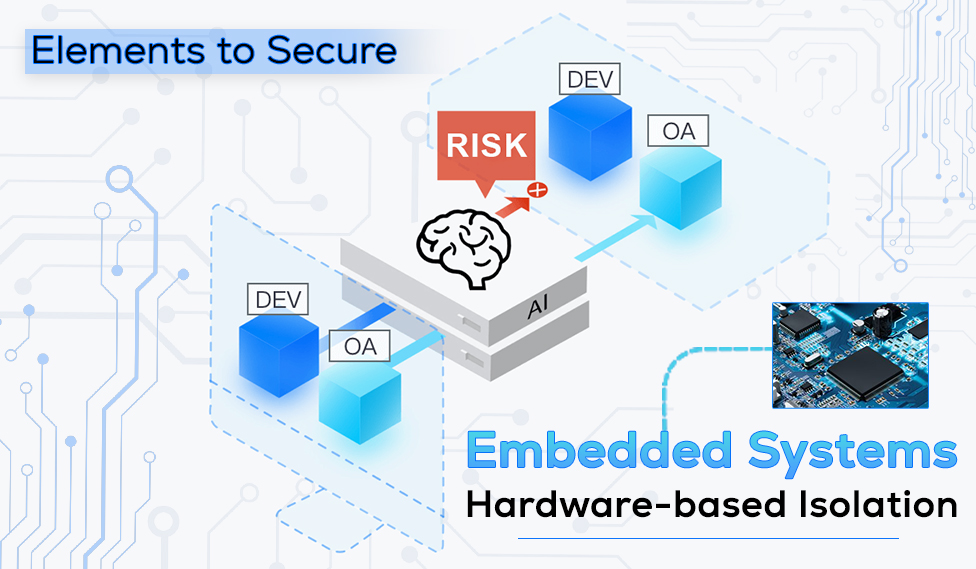
Hardware-based isolation
Embedded developers should remember the first step to security is through isolation. Any critical system must be separate from the rest. This step will confine the risk to a specific network in case of a hack.
Therefore, it is best to isolate applications into various domains and control each of them with their own set of access and privileges.
In a conventional embedded system, the architecture is so that a module can gain access to the entire network. If a hacker gets hold of a single component, they quickly get hold of the whole system.
1 – Processor structure
A developer must use a microcontroller with hardware-based isolation. It will divide the execution environment into two; Secure and unsecured network.
The secure network manages memory, peripherals, and functions that are vital for the system’s security. An unsecured network is the conventional, rich execution network.
In the latest microcontrollers, isolation happens in two methods, either by using Cypress PSoC 64 or with a single-core isolation system such as TrustZone.
Multi-Core microcontrollers perform hardware-based isolation by assigning one microcontroller to the secure system and another to the non-secure system.
2 – Memory Protection Units (MPUs)
MPUs are a secondary isolation layer on top of the primary one. It can be integrated into security systems and enhance the application’s integrity. A majority of microcontrollers would have MPUs in both secure and unsecured networks.
Memory Protection Units establish further boundaries within the system that restricts tasks and functions. They have control over the scope of a task in a specific process. Therefore, the task will perform nothing outside the purview of the process in question.
If the functions access something beyond their region, the MPUs will notice this violation and intervene to prevent unauthorised entry. Hence, the MPUs can establish secured partitions that isolate the components.
3 – PPUs & SMPUs
PPUs and SMPUs aid the developer to create extra levels of security and sharing memory content. Hence they are referred to as Shared memory protection units (SMPUs).
The SMPU can recognise different security contexts inside the processor. It can even identify the difference between secure and unsecured access. This isolation tool comes in handy for developing many levels of protection and control measures in a process.
Embedded developers can use Peripheral protection units (PPUs). This tool handles access to various blocks like USB, SPI, UART, etc. These accesses happen in multiple contexts managed by SMPUs that ensure the safety of the context within other MPU contexts running on different cores inside the microcontroller.
Conclusion
A developer can ensure the security of the embedded systems through the applications mentioned in this blog. They can isolate and create barriers to keep third parties away from the network.



 +1.585.935.7123
+1.585.935.7123 +91-804-148-6861
+91-804-148-6861